In today’s digital-first world, organizations face an ever-growing number of cyber threats. From phishing attacks and ransomware to misconfigured systems and unpatched software, poor security practices can quickly expose businesses to serious risks. This is where strong cyber hygiene becomes essential. ThreatAware’s centralized cybersecurity platform is designed to help organizations manage, monitor, and protect their IT assets while improving overall cyber hygiene across the enterprise.
What Is Cyber Hygiene and Why It Matters
Cyber hygiene refers to the routine practices and processes that organizations follow to maintain the health and security of their IT systems. Just like personal hygiene prevents illness, good cyber hygiene helps prevent security breaches, data loss, and operational downtime. This includes asset visibility, regular updates, vulnerability management, access control, and continuous monitoring.
Without proper cyber hygiene, even advanced security tools can fail. Unknown devices, outdated software, and unmanaged user access create gaps that attackers can easily exploit. ThreatAware addresses these challenges by providing a centralized view of your entire IT environment.
Centralized Visibility for Better Asset Management
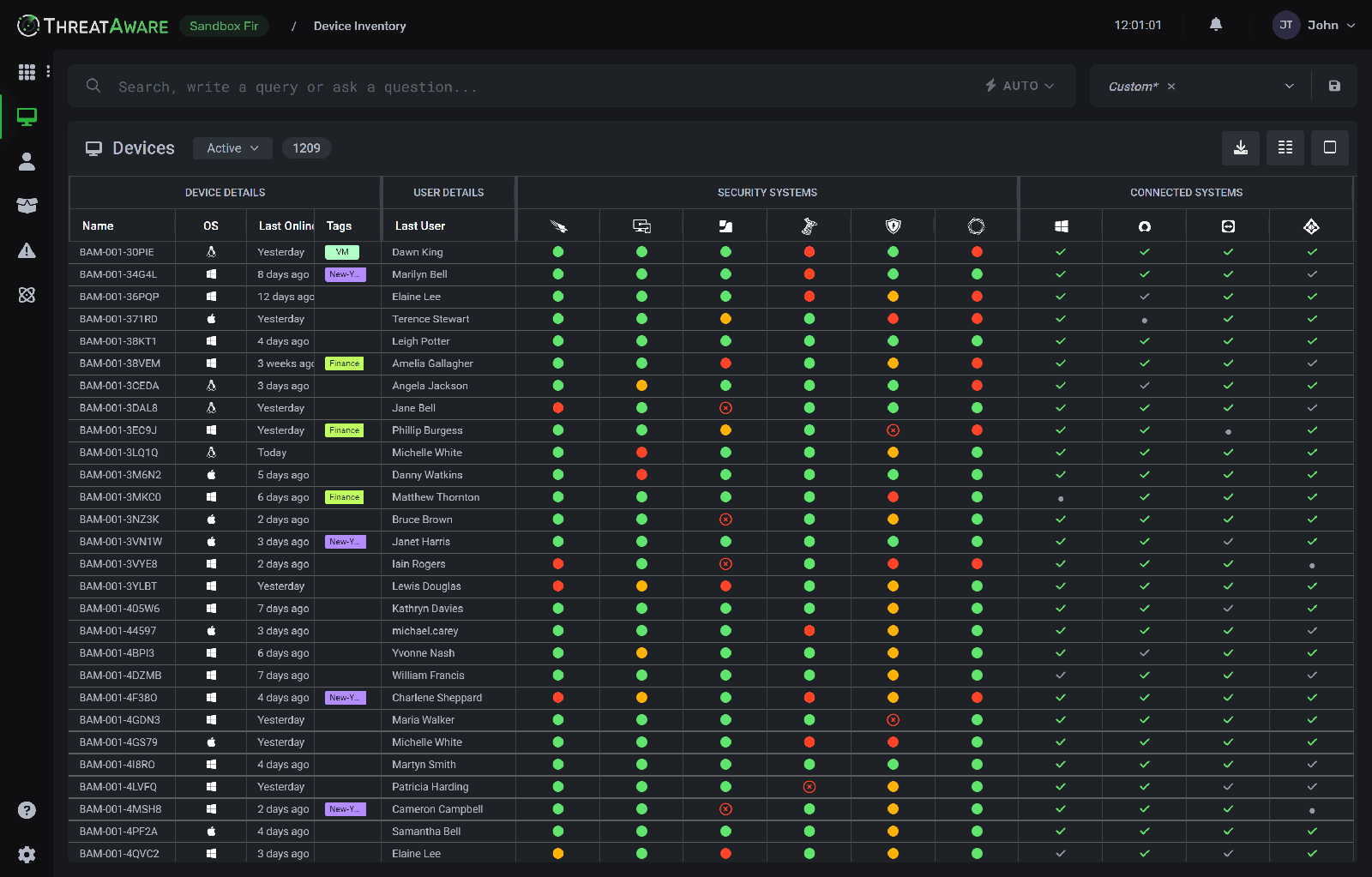
One of the biggest challenges organizations face is knowing exactly what assets they have and where vulnerabilities exist. ThreatAware’s platform offers centralized asset discovery and management, allowing security teams to identify devices, users, and systems across the network. This visibility is a critical foundation of effective cyber hygiene.
By maintaining an accurate and up-to-date inventory of IT assets, organizations can reduce blind spots, prioritize risks, and ensure that no critical system is left unprotected.
Streamlined Security Operations
ThreatAware simplifies cybersecurity by consolidating key security functions into a single, easy-to-use platform. Instead of juggling multiple tools, teams can manage threats, monitor system health, and respond to incidents from one dashboard. This streamlined approach not only saves time but also improves consistency in security practices.
Strong cyber hygiene depends on repeatable, automated processes. ThreatAware supports this by helping organizations standardize security policies, track compliance, and reduce human error.
Proactive Threat Detection and Risk Reduction
Maintaining cyber hygiene is not just about prevention—it also involves early detection. ThreatAware continuously monitors your environment for suspicious activity, misconfigurations, and potential threats. By identifying risks early, organizations can take action before small issues turn into major incidents.
This proactive approach reduces the likelihood of breaches, minimizes downtime, and protects sensitive data. It also supports regulatory compliance by demonstrating ongoing risk management and security oversight.
Scalable Security for Growing Organizations
As businesses grow, so do their IT environments. New users, devices, and applications can quickly increase complexity. ThreatAware’s centralized cybersecurity platform is built to scale, making it easier to maintain cyber hygiene as your organization evolves.
Whether you are a small business or a large enterprise, ThreatAware adapts to your needs while ensuring consistent security standards across all systems.
Why Choose ThreatAware
ThreatAware empowers organizations to take control of their cybersecurity posture through visibility, automation, and continuous monitoring. By improving cyber hygiene, businesses can reduce attack surfaces, strengthen resilience, and protect critical assets more effectively.
Final Thoughts
Good cyber hygiene is no longer optional—it is a fundamental requirement for modern organizations. ThreatAware’s centralized cybersecurity platform provides the tools and insights needed to manage and protect IT assets with confidence. Schedule a demo today to see how ThreatAware can streamline your security operations, strengthen your cyber hygiene, and help safeguard your business against evolving threats.

Write a comment ...